Implementing Identity and Access Management solution based on AWS and Keycloak
Contents

Problem
If you work with a lot of different AWS accounts, you have to create different YAML users for each account and remember logins and passwords.
-
— Creation of multiple accounts in different web apps.
-
— Too much time for management and setting AWS apps accounts, Gmail accounts
-
— Mixing up different passwords to these accounts, finding the way to securely store them.
-
— Authorization and data storage for applications.
-
— Potentially high costs for using Auth0, Rippling, Gmail SSO solutions etc.
Federate access to AWS account.
Solution
For solving all these problems we used a Keycloak identity provider. It’s an open source project from Redhat. You can learn more about Keycloak here.
We used AWS services such as EC2, ALB, ECS, RDS, CodePipeline, and ECR. - ECS: for managing docker containers.
-
— EC2: for hosted docker containers.
-
— ALB: for distribution of data.
-
— RDS: for saving the data of users (password, email, names etc).
-
— CodePipeline: for automatization of deployment.
-
— ECR: for saving modified docker images.
-
— SES: for send email to users
Overall cost of this solution: $1.61/day
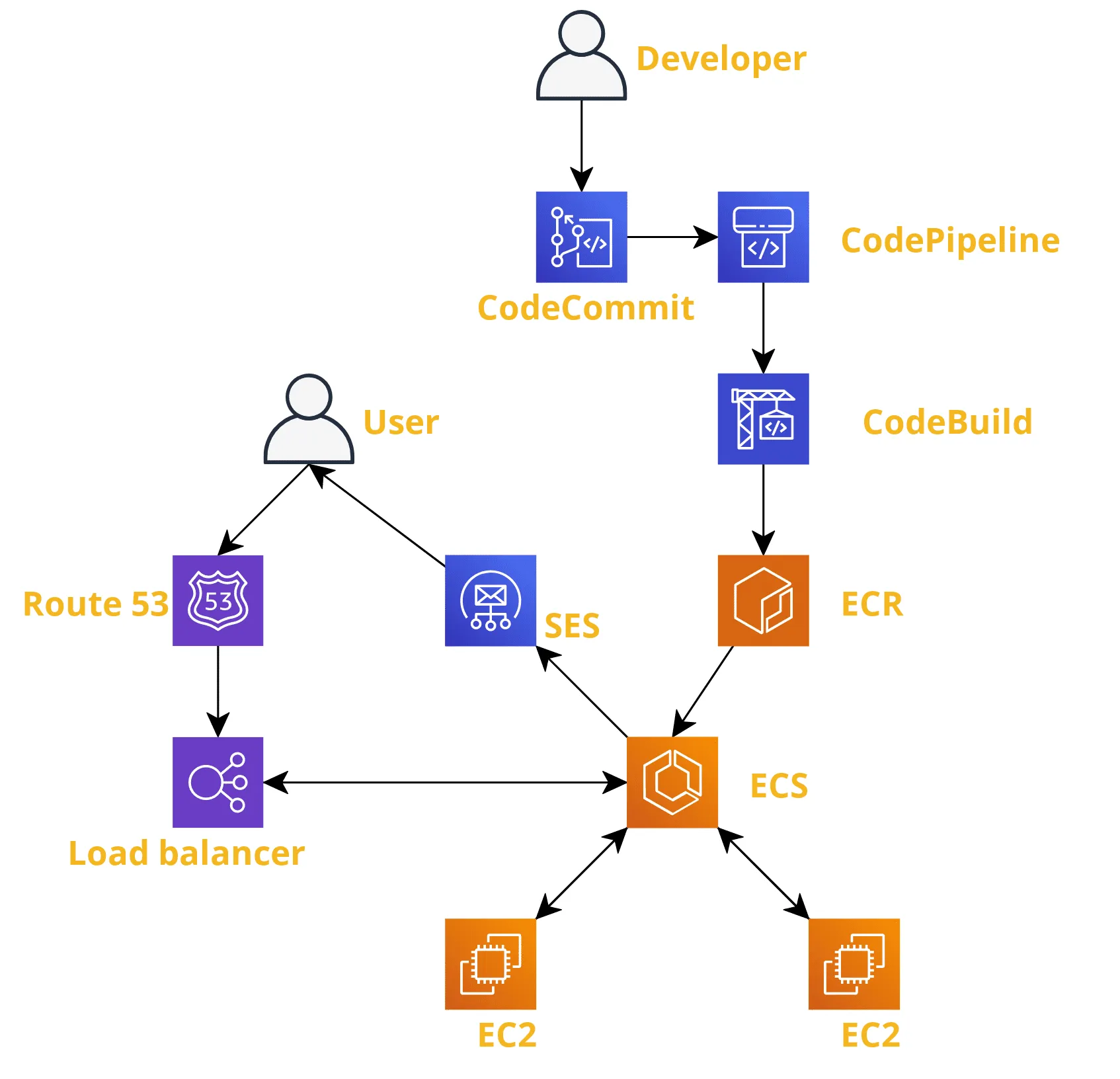
The diagram represents the pipeline process of how the custom docker image is created and how the system works.
We have customized the start page, authorisation page and admin panel. Moreover we can sent a forgotten password email using AWS SES. This solution is beneficial because we can send more emails than when using other providers. When creating custom containers, we can change the UI, text in email, and other parameters.
Advantages
-
— In comparison to Google Suite, Rippling and Auth0 SSO our Keycloak solution has full access to the server and hosted on our own AWS account. It gives availability to optimize and customize themes, pages, modules and providers.
-
— You are the only one who have access to the data of the user - Possibility to manage security for access. You can limitate the access to Keycloak by IP address (it’s up to you to decide how many users will have access to the app).
-
— Keycloak we can use to replace rippling and okta
-
— Additional encryption of sensitive data.
-
— We can increase the volume in RDS, or CPU, and other parameters to take more clients
-
— Better price (Keycloak SSO - $0.4 per-user/month, Google Suite SSO - $6 per-user/month)
Who needs this?
Companies which:
- — Do not want other persons to have access to their data
- — Do not want to create their own solutions for authorization in applications
- — Want to be able to customize
- — To save money
